Administrative Rights and Installing Software
To better protect our community, CNS will be making changes to ESF computers to better align ESF best practices with SUNY/State/Federal requirements. Specifically, all Faculty and Staff will have standard user accounts on ESF computers. In an effort to continue to provide Faculty and Staff with the ability to install software as needed CNS is implementing a privileged access management (PAM) tool called ThreatLocker. Through a variety of different mechanisms, ThreatLocker allows anyone on campus to install applications that have been previously requested and approved. If you are installing something new to ESF, you will be prompted to submit a request from Threatlocker and notified once the application has been reviewed.
Requesting and Installing a New Application
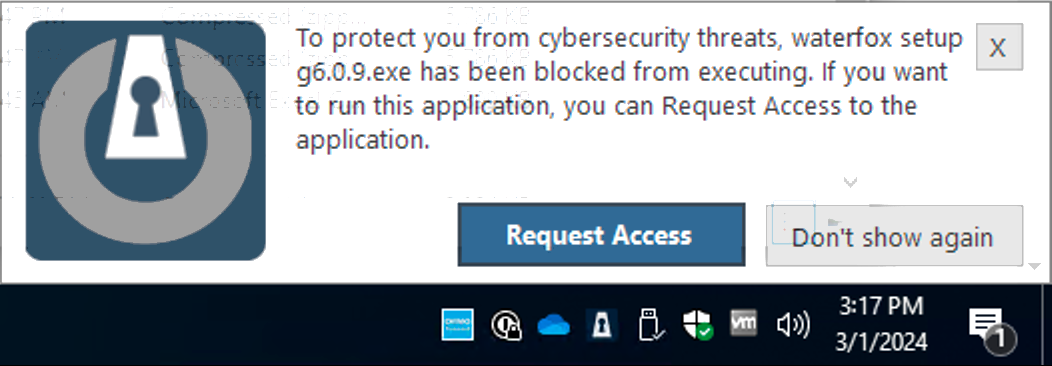
When a program that has not been previously approved is opened you will receive a popup.
- If you did not open anything, click Don’t Show Again
You will not be bothered with this popup again in the future for this program; it will be silently blocked.
- If you need this program for work, click Request Access
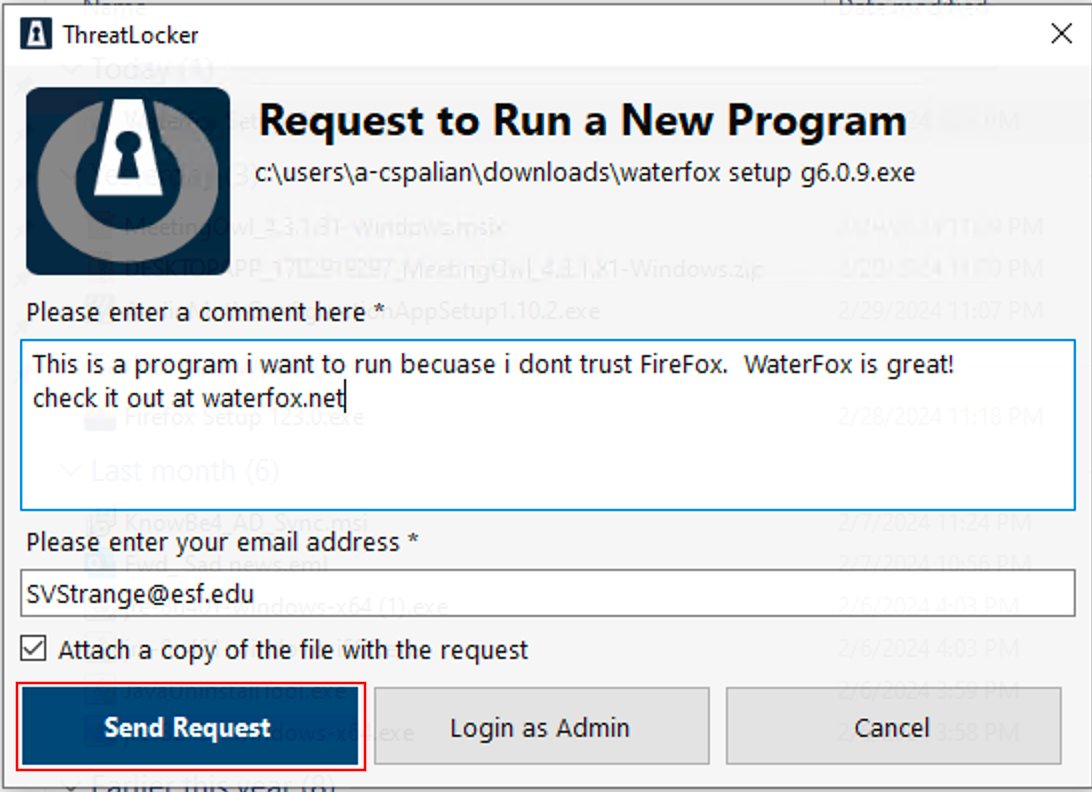
In the new pop-up window, please include the following information:
- What is the application for
- Does more than one person at ESF use this program on this computer
- Was the application obtained from the official site
- Your esf email address
Once you have filled out the form, click Send Request
Once the request has been approved or denied you will receive a notification to the email address you provided when submitted the request.
Requests will be responded to within 2 business days. If your request has been approved you can go ahead and re-run the program.
Running a Previously Requested Application
If the application has been previously request and approved, you will be able to run the program without any need to contact CNS.
If the application has been previously request but denied, you will receive the follwing pop-up:
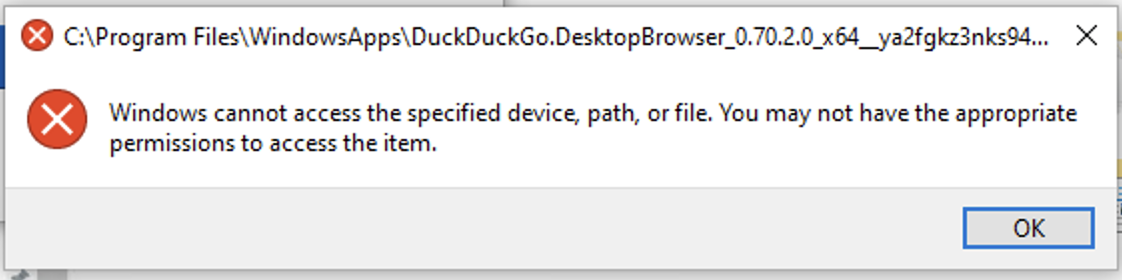
If you need this application please contact helpdesk@esf.edu with the following information:
- What is the name of the application
- What is the application for
- Does more than one person use it on this computer
- Was the application obtained from the official site